be prepared Protected Safe
Security is not an option – it is a necessity.”
“We ensure that your data remains safe!
We prepare you for every possible cyber challenge.
Our team assesses risks, uncovers vulnerabilities, and provides constant support when you need it most.
Ensure the operational stability of your data – we test your systems and websites, offer endpoint protection, intrusion detection, antivirus solutions, monitoring programs, audits, GDPR compliance, and much more.
Don’t let hackers stay one step ahead of you –
Build a strong digital defense today.
Basic Security Package
Complete protection for your business from the most common cyber threats!
This package includes key modules to protect your devices, network, and data, preventing viruses, hacking attacks, and phishing threats in real time.
Security Solutions
Complete protection of your data from all types of cyber threats with advanced security solutions tailored to your needs.
Detects and blocks viruses, trojans, spyware, and ransomware on Windows, macOS, and Linux.
Ransomware prevention – Blocks applications trying to encrypt your files before damage occurs.
Detects and prevents programs attempting to steal your passwords through keystroke logging.
Unknown malware detection – Analyzes suspicious activities and blocks new threats that traditional antivirus might miss.
Prevents attacks through software vulnerabilities – If you use outdated or unpatched software, hackers can exploit its weaknesses and infect your system.
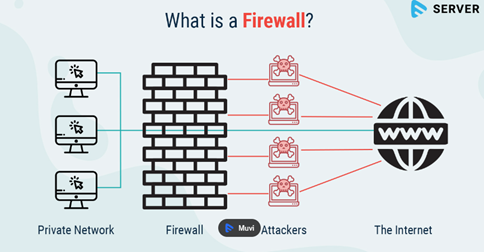
Blocks unauthorized access – The firewall acts like a security guard at the door, checking who is allowed and not allowed to enter your network. If a hacker tries to gain access, the firewall blocks them.
Filters internet traffic – It checks which applications and devices are communicating with the internet, preventing suspicious connections and unwanted programs from sending data.
Blocks malicious websites – If you accidentally click on a dangerous link, the firewall can block the site before it downloads a virus to your computer.
networks – Even if you use public Wi-Fi.
Detects and stops suspicious traffic.
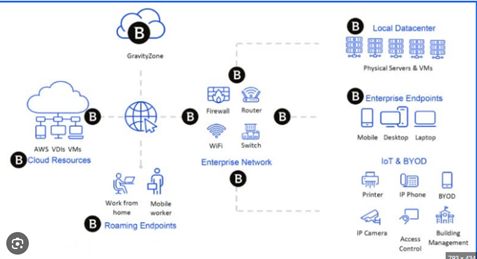
Protects various types of devices – Computers, laptops, mobile devices, servers, cloud resources, IoT devices, routers.
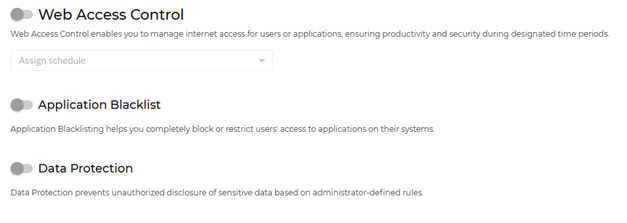
Blocks dangerous websites – If a link leads to a website with viruses, phishing, or malicious software, Content Control.
Restricts access to inappropriate sites.
Filters internet traffic.
Blocks fake websites – If a user clicks on a link in a fraudulent email.
Prevents phishing attacks over the internet – If you open a website that impersonates a legitimate platform (bank, email service, social network),

Restricts the use of unknown devices.
Data theft protection.
Works on all devices in the network .
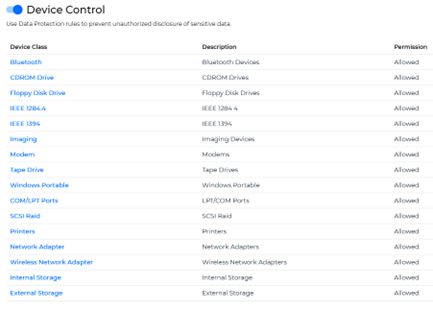
Restricts use of unknown devices.
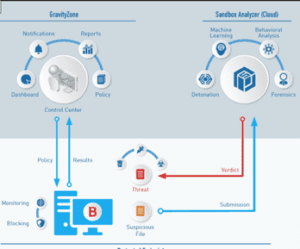
In addition to all features from the Basic Security Package, this package adds even stronger security layers, including automatic analysis of suspicious files (Auto Sandbox Analyzer) and HyperDetect – advanced technology for early detection of complex threats.
Automatically tests suspicious files. Detects and blocks hidden threats. Stops threats before they infect your computer.
Detects advanced and invisible threats. Uses artificial intelligence (AI) for analysis. Provides an additional layer of protection before an attack activates. 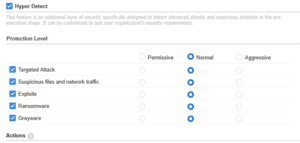
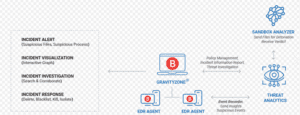
Contains everything from Business Security Premium, but adds powerful attack detection and response with EDR (Endpoint Detection and Response).
Additionally, it enables XDR sensors for broader security analysis.
Key benefits:
Advanced threat investigation – Event history and real-time analysis enable fast attack identification.
EDR (Endpoint Detection and Response).
- Ability to add XDR sensors
Email Security
Blocks phishing and fraudulent emails – It filters all incoming messages and prevents phishing attacks that attempt to steal your passwords, banking information, or confidential data.
Prevents sending malicious attachments – Automatically scans attached files for viruses and malware before you open them.
Detects and blocks spam and unwanted messages – Reduces the risk of opening potentially dangerous messages and eliminates unnecessary spam messages that waste your time.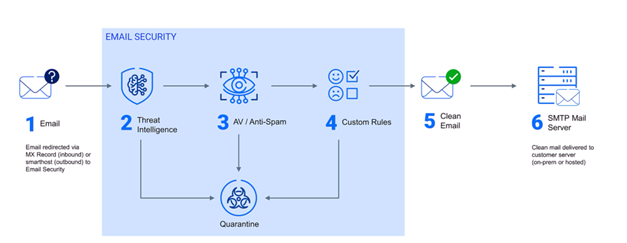
Blocks mobile threats in real time – Prevents viruses, phishing, ransomware, and network attacks targeting mobile devices.
Protects corporate and BYOD devices – Ensures access to confidential data regardless of whether the device is corporate-owned or personal.
Recognition of risky applications – Performs automatic vetting of applications and warns about unsafe or illegitimate apps that could compromise security.
Automatic software updating and patch management
Automatic software updates
Review and control of updates – Administrators can schedule security updates to apply when they do not disrupt workflows.
Automatic vulnerability scanning – The system monitors published vulnerabilities (CVE) and suggests urgent updates to protect against the latest threats.
Penetration testing protects your system from real hacker attacks by simulating cyber-attacks to find and close security weaknesses before hackers can exploit them.
How does penetration testing protect you?
Vulnerability discovery – Scans networks, servers, applications, and user systems for potential security gaps.
Simulated hacker attacks – Tests your system’s response to various attacks, including social engineering, SQL injection, brute force, and ransomware simulations.
Improvement recommendations – Provides detailed reports with suggestions to fix vulnerabilities and enhance security.
Penetration testing involves expert testers performing both automated and manual tests to identify entry points and weaknesses in hardware, software, and human factors. They then report findings and provide guidance for proper controls. This proactive security measure helps organizations prevent unauthorized access, data breaches, financial loss, and damage to reputation by addressing vulnerabilities early.
Hacker forums and Darknet marketplaces are places where stolen data is sold. Darknet investigation helps verify whether your passwords, email, or confidential information have been compromised and are accessible to attackers.
How does Darknet investigation protect you?
Checking hacker forums and databases – Detecting whether your user data, passwords, or financial information have been sold or shared on the Darknet.
Identification of potential threats – If your company is targeted by phishing campaigns or organised attacks, this service can reveal warning signs.
Protection before it’s too late – If your data is found, measures are taken to change passwords, improve security, and notify affected users.
Ensure your company is compliant with the Personal Data Protection Act in Macedonia! Our service provides complete protection of sensitive information, preventing misuse and unlawful data processing.
How does this service protect you?
Identification and management of personal data – We analyze all data your company processes and ensure they are classified and protected in accordance with legal regulations.
Website compliance with legal requirements – We ensure your website meets all personal data protection regulations, including clear privacy policies, data processing consents, and security of user information.
Preparation for legal compliance – Your company will be fully compliant with Macedonia’s Personal Data Protection Act, avoiding fines and legal risks.
